Ever lost a document, had a system malfunction because of a new driver or software installation or had a virus impact your files? I'm pretty sure I know the answer to this question.
To avoid such situations consider using the volume shadow copy feature. The feature is on by default in Windows 7 and easily added to Vista.
The feature allows you to launch System Restore and roll back to a working system state from before the installation. If you can’t get your system to boot, you can also do this from the Windows Setup DVD. This process is reversible, i.e. your current state will be automatically saved as a restore point, to which you can later go back.
In another situation, if you accidentally delete 10 pages of your dissertation, you can right-click the document, choose Restore previous versions, and access a previous version of it. You can open it (in read-only mode) or copy it to a new location.
If you accidentally delete a file or folder, you can right-click the containing folder, choose Restore previous versions, and open the folder as it appeared at the time a shadow copy was made (see screenshot below). All the files and folders that you deleted will be there.
I made sure I had the feature turned on based on past painful experiences. Something to consider...
Happy holidays
Thursday, December 24, 2009
Monday, December 21, 2009
Security Makes the Headlines Again....
Interesting article in the WSJ recently about a tool called Skygrabber that insurgents are using to intercept video feeds from US drones over Iraq and Afghanistan. Of course the attention has overwhelmed the skygrabber.com website and is a lesson on being ready for your moment when it arrives but, the real issue here is one of security and how commercial enterprises are thriving on attacking vulnerabilities in networks and making a profit in doing so.
Here is a quote from Andrew Solonikov, one of the software’s developers.
"It (the software) was developed to intercept music, photos, video, programs and other content that other users download from the Internet -- no military data or other commercial data, only free legal content," he said by email from Russia.
Um, last time I checked, “free, legal content” can be downloaded and does not need to be intercepted. Intercepted is what you do when others own the content and you want to steal it. Looks like Andrew and friends don’t mind stealing from musicians, movie producers and software companies but, don’t want to mess with the military.
Any bets that the US intel community is capable of monitoring who downloads this software?
Here is a quote from Andrew Solonikov, one of the software’s developers.
"It (the software) was developed to intercept music, photos, video, programs and other content that other users download from the Internet -- no military data or other commercial data, only free legal content," he said by email from Russia.
Um, last time I checked, “free, legal content” can be downloaded and does not need to be intercepted. Intercepted is what you do when others own the content and you want to steal it. Looks like Andrew and friends don’t mind stealing from musicians, movie producers and software companies but, don’t want to mess with the military.
Any bets that the US intel community is capable of monitoring who downloads this software?
Thursday, December 10, 2009
Home Networking Security...Beware
Guess what happened to me the other day? I was using a DynDNS service to remote into my house and mis-typed the IP address. Instead of being rejected, I was provided a prompt to a DVR system login (I don’t have a DVR). I did a quick Google search for default DVR username/passwords and found a large list of common username and passwords.
It’s amazing how many home devices are now IP enabled, but also concerning when you think about how many people are still using the default password info that comes with the device.
Hopefully it becomes common practice for everyone (inside our industry and outside of it) to change the default information, whenever they get a new device.
P.S.
Did you know there will be 215 million IP enabled devices by 2012?
It’s amazing how many home devices are now IP enabled, but also concerning when you think about how many people are still using the default password info that comes with the device.
Hopefully it becomes common practice for everyone (inside our industry and outside of it) to change the default information, whenever they get a new device.
P.S.
Did you know there will be 215 million IP enabled devices by 2012?
Friday, December 4, 2009
Put your Day on Auto Pilot with PowerShell Scripting…
Ok I wish it were that simple, but, it is possible to save substantial time and effort by automating many repetitive and common Windows IT tasks by creating scripts with PowerShell. There are lots of websites and books that have pre-written scripts for you. So, not only can you automate a good chunk of your IT tasks, you can copy and paste your way to automation. With that in mind, here are a few resources I’ve found helpful.
Microsoft Technet
The premier place for basic and advanced topics related to PowerShell. I’ve spent hours on this site and it has everything from training and free scripts to a download center with lots of goodies. Here are some MUST visit sections:
Library – More reading than I could possibly do this year. It’s the place to start with good example code to walk you through the learning process.
Download Center – Get PowerShell and the scriptomatic2 software to make scripts using a graphical user interface.
Scripts – Over 650 scripts on items from managing an IIS server to system backups and restores. Once you know how to use PowerShell, jump start your library here.
PowerShell.com
A great website with tips, tools, a forum, free scripts and lots more on PowerShell.
CBT Nuggets
CBT Nuggets provides an excellent online training program that covers PowerShell. Their sample tutorial is a pretty good primer on several basic commands and the PowerShell pipeline concept (like a workflow).
Quick Reference Card/Cheat sheet
DZone makes a nice set of free cheat sheet reference guides. These are handy to have printed and around when making/editing scripts.
Twitter
For Twitter users, you may want to follow these users:
http://twitter.com/powertip - Tip of the day tweets
http://twitter.com/ScriptingGuys - Tips and ideas straight from Microsoft
http://twitter.com/shitmydadsays - Because it’s funny
Microsoft Technet
The premier place for basic and advanced topics related to PowerShell. I’ve spent hours on this site and it has everything from training and free scripts to a download center with lots of goodies. Here are some MUST visit sections:
Library – More reading than I could possibly do this year. It’s the place to start with good example code to walk you through the learning process.
Download Center – Get PowerShell and the scriptomatic2 software to make scripts using a graphical user interface.
Scripts – Over 650 scripts on items from managing an IIS server to system backups and restores. Once you know how to use PowerShell, jump start your library here.
PowerShell.com
A great website with tips, tools, a forum, free scripts and lots more on PowerShell.
CBT Nuggets
CBT Nuggets provides an excellent online training program that covers PowerShell. Their sample tutorial is a pretty good primer on several basic commands and the PowerShell pipeline concept (like a workflow).
DZone makes a nice set of free cheat sheet reference guides. These are handy to have printed and around when making/editing scripts.
For Twitter users, you may want to follow these users:
http://twitter.com/powertip - Tip of the day tweets
http://twitter.com/ScriptingGuys - Tips and ideas straight from Microsoft
http://twitter.com/shitmydadsays - Because it’s funny
Wednesday, November 25, 2009
Are Businesses Prepared for Workforce Disruptions? New Cisco Study Says No…
I’ve recently discussed keys to avoiding network failures and tips to being prepared for network disasters. A recent study by Cisco highlights the need to continually keep network continuity at the forefront of our minds.
The survey finds that organizations are not ready to operate as usual during workforce disruptions because they haven’t set-up the proper networking infrastructures to support remote work by a high percentage of their employees.
Here are some of the highlights of the survey:
- 74 percent of the 502 IT decision-makers surveyed said that fewer than half of their employees were currently set up to work remotely.
- Asked why more employees did not have remote access, 38 percent said that business requirements did not necessitate it.
- Only 22 percent of those top decision makers felt that their current remote access solutions have contributed to their disaster preparedness.
- Just 15 percent of the respondents listed "pandemic or other disaster preparedness" as a top business driver for providing remote access to employees, and only 5 percent listed it as the primary business driver.
The study suggests that organizations are more focused on business needs under normal conditions than on remote access for business continuity purposes. In this economic environment that is not so surprising. Of course, it only takes a road closing, really bad weather or widespread illness that affects employee productivity and company revenue to change that focus.
Cisco also posted a YouTube video with a preview of the findings from the survey, if you’re interested in more details.
The survey finds that organizations are not ready to operate as usual during workforce disruptions because they haven’t set-up the proper networking infrastructures to support remote work by a high percentage of their employees.
Here are some of the highlights of the survey:
- 74 percent of the 502 IT decision-makers surveyed said that fewer than half of their employees were currently set up to work remotely.
- Asked why more employees did not have remote access, 38 percent said that business requirements did not necessitate it.
- Only 22 percent of those top decision makers felt that their current remote access solutions have contributed to their disaster preparedness.
- Just 15 percent of the respondents listed "pandemic or other disaster preparedness" as a top business driver for providing remote access to employees, and only 5 percent listed it as the primary business driver.
The study suggests that organizations are more focused on business needs under normal conditions than on remote access for business continuity purposes. In this economic environment that is not so surprising. Of course, it only takes a road closing, really bad weather or widespread illness that affects employee productivity and company revenue to change that focus.
Cisco also posted a YouTube video with a preview of the findings from the survey, if you’re interested in more details.
Monday, November 23, 2009
5 Key Common Culprits for Single Points of Network Failures
I recently wrote a post about network disaster preparedness and provided some tips on how to avoid network outages. I came across a great blog post that added more depth to the topic by discussing how to avoid the most common culprits for single points of failure on small to midsize networks. The post was written by Derek Schauland from TechReuplic and he highlights some network areas that I agree need particular attention.
1. Network Switches – Keeping spare switches online is ideal, but may be cost prohibitive. Consider having a couple of extra switches around in case of a failure.
2. Tape Drives – Ensure you have redundancy in terms of tape drives for back-up and recovery in case of a worst case scenario. You never know when a tape drive may stop working.
3. Network Interface Cards (NICs) – Use servers with multiple NICS for improved connectivity and for failover in case one of the cards in the server fails.
4. Internet Connections – Having redundant connections can be a critical part of avoiding a single point of failure, especially considering the importance of the Internet to business operations these days. Of course the cost of keeping a connection with two providers active needs to be justifiable for your business. At a base level, it never hurts to have a plan in place to immediately take action to move to a secondary provider if your primary fails.
5. Cabling – I’m adding to Derek’s list here, but cabling issues often cause LAN failures. It’s always worthwhile to have many spare cables of different lengths ready to go. I keep a few really long ones as spares in every telco/IT room. They are great for testing and at times when I need a temporary cable.
This will help you to solve, both the most basic and overlooked issues and the more dramatic ones. This list is not all inclusive, but these fives areas should be considered in planning for a worst case scenario. Do you have any additional areas that you pay particular attention to in your network?
1. Network Switches – Keeping spare switches online is ideal, but may be cost prohibitive. Consider having a couple of extra switches around in case of a failure.
2. Tape Drives – Ensure you have redundancy in terms of tape drives for back-up and recovery in case of a worst case scenario. You never know when a tape drive may stop working.
3. Network Interface Cards (NICs) – Use servers with multiple NICS for improved connectivity and for failover in case one of the cards in the server fails.
4. Internet Connections – Having redundant connections can be a critical part of avoiding a single point of failure, especially considering the importance of the Internet to business operations these days. Of course the cost of keeping a connection with two providers active needs to be justifiable for your business. At a base level, it never hurts to have a plan in place to immediately take action to move to a secondary provider if your primary fails.
5. Cabling – I’m adding to Derek’s list here, but cabling issues often cause LAN failures. It’s always worthwhile to have many spare cables of different lengths ready to go. I keep a few really long ones as spares in every telco/IT room. They are great for testing and at times when I need a temporary cable.
This will help you to solve, both the most basic and overlooked issues and the more dramatic ones. This list is not all inclusive, but these fives areas should be considered in planning for a worst case scenario. Do you have any additional areas that you pay particular attention to in your network?
Tuesday, November 17, 2009
HP Buys 3Com… What Does It Mean for the Networking Market?
The recent acquisition of 3Com by HP makes me wonder what they are going to do in the networking market. For some time, we have been using HP Procurve switches along side Cisco gear. They have proven reliable and very cost effective. I have been looking forward to HP enchancing its offerings. In light of Cisco expanding into the server market, there was an expectation that HP would more aggressively address the networking market and create better choices for lower cost networking devices. It just doesn’t seem like the 3Com product line is sufficient for HP to go head-to-head with Cisco. This makes me think that HP is not even close to being done from an acquisition standpoint. I wonder when we will see HP drop another huge chunk of change to buy another device vendor. And who will the vendor be?
Anybody want to comment on who they think HP will buy next or do you think 3Com products sufficiently supplement the HP Procurve line?
Anybody want to comment on who they think HP will buy next or do you think 3Com products sufficiently supplement the HP Procurve line?
Friday, November 13, 2009
Want to Become a Service Provider CEO? Try Cisco’s New Simulation Game…
Looking to try your hand at being a CEO for a day without all the real life pressures? Here’s your chance. Cisco has a free Sim City type real time strategy simulation game called myPlanNet, you can download (only works on Windows though). If you want a preview before downloading (40mbs in size) the game, check out the YouTube video.
You have to register (if you don’t already have an account) to get the game, but it’s worth the hassle. The point of the game is to manage your service provider business as the CEO as it evolves from the dial-up, through to the broadband and mobile connected eras and into the future age of networking.
Cisco created the game as a marketing and educational tool and I’ll admit it is a lot more fun than reading a white paper. Check it out and let me know what you think.
You have to register (if you don’t already have an account) to get the game, but it’s worth the hassle. The point of the game is to manage your service provider business as the CEO as it evolves from the dial-up, through to the broadband and mobile connected eras and into the future age of networking.
Cisco created the game as a marketing and educational tool and I’ll admit it is a lot more fun than reading a white paper. Check it out and let me know what you think.
Tuesday, November 10, 2009
5 Easy Steps to Enabling SNMP on Cisco’s Unified Communications Manager for VoIP Monitoring
One of our offices has the new Unified Communications Manager (UCM) 6.1, the software-based call-processing component of the Cisco VoIP solution. Did you know that UCM supports SNMP monitoring? Based on a few conversations I had with people there seemed to be some confusion about the topic.
There is a good reason for the confusion. I was doing some SNMP polling and could not get the metrics to appear. It turns out that all previous versions of UCM supported SNMP by default, however the current version requires you to enable the protocol. After a bit of research I found that you need to enable SNMP on both the host server and the Unified Communications Manager application.
With both sets of SNMP services enabled, I was able to monitor both the health and status of the core system and gather quite a few metrics regarding the service. I’ll share a few of my favorite monitoring metrics and some associated screenshots in a later post.
For those of you, who already monitor your Unified Communications Manager with SNMP, let me know what you find useful. For those of you who have not turned on SNMP, here are the steps:
1. Open the web console to CCM
2. In the Navigation dropdown in the upper right, select Cisco Unified Servicability
3. Go to Tools / Service Activation
4. Select Cisco CallManager SNMP Service
5. Click the Save button
Here is a link to where I found the Cisco UCM MIBS.
There is a good reason for the confusion. I was doing some SNMP polling and could not get the metrics to appear. It turns out that all previous versions of UCM supported SNMP by default, however the current version requires you to enable the protocol. After a bit of research I found that you need to enable SNMP on both the host server and the Unified Communications Manager application.
With both sets of SNMP services enabled, I was able to monitor both the health and status of the core system and gather quite a few metrics regarding the service. I’ll share a few of my favorite monitoring metrics and some associated screenshots in a later post.
For those of you, who already monitor your Unified Communications Manager with SNMP, let me know what you find useful. For those of you who have not turned on SNMP, here are the steps:
1. Open the web console to CCM
2. In the Navigation dropdown in the upper right, select Cisco Unified Servicability
3. Go to Tools / Service Activation
4. Select Cisco CallManager SNMP Service
5. Click the Save button
Here is a link to where I found the Cisco UCM MIBS.
Friday, November 6, 2009
Random Netflow – A Tool to Keep in Your Kit
In my network management adventures throughout the years, I’ve found Netflow to be an invaluable tool to troubleshoot a range of network issues – from bandwidth to service and resource problems. It’s an amazing traffic mining tool – it analyzes traffic flows across a network and provides a huge amount of information. That is where the problem lies as well – sometimes Netflow delivers too much information when I just want a small amount data for planning and traffic engineering. I’m sure you’ve come across this issue – right?
I know I’m not the only one, since I came across a great article from Network World on how to solve this issue. The advice is very straight forward and concise on how to solve the information overload issue by using the random Netflow feature. Thought it was worth sharing.
I know I’m not the only one, since I came across a great article from Network World on how to solve this issue. The advice is very straight forward and concise on how to solve the information overload issue by using the random Netflow feature. Thought it was worth sharing.
A few of my favorite tips from the article:
- Know your flow. Netflow versions 5 or 9 work if you need to export the data to look at it off device. With other versions you can view the data on the device.
- You can not have Netflow enabled on an interface you want to run random Netflow on. A device always gives full Netflow precedence over random Netflow.
- If you run into any problems there is a debug command: debug flow-sampler.
What was your favorite tip? Or if you have one that isn’t mentioned, I’d love to hear it!
Wednesday, November 4, 2009
Slow Bandwidth? Remove Unused Protocols to Improve Speed
Identifying protocols that contribute to slow bandwidth
I’m always looking for easy and effective ways to improve network performance. When I’m unhappy with network performance I try removing unused protocols to help lower traffic and increase network speed. Have you found any other effective methods that you want to share with us?
To give this one a try, check the default network protocol settings used when installing operating systems and network drivers. They often include protocols such as IPv6, LLMNR and PGM, which are not commonly used in most networks. For example, if you have Microsoft Vista, you’re wasting traffic with the IPv6 protocol running, unless you’re actually using IPv6. If you remove it, you’ll open up your network and improve speed.
Common unnecessary protocols
IPv6
Microsoft ships IPv6 as one of the default protocols on Windows Vista and Windows 2008. While IPv6 may be a replacement for IPv4, it is not yet a standard protocol for most networks. Auto enabling all devices with IPv6 may be a bit ambitious, since most LANs and WANs simply are not yet supporting IPv6. Check out this Microsoft article on how to remove IPv6.
IPX Network client
 If you’re not using Netware, don’t leave the IPX (Internetwork Packet Exchange) Network client installed. Sometimes it’s left over on older systems and can easily be removed. Uncheck the Client Service for Netware box and reboot the system (see Figure 1).
If you’re not using Netware, don’t leave the IPX (Internetwork Packet Exchange) Network client installed. Sometimes it’s left over on older systems and can easily be removed. Uncheck the Client Service for Netware box and reboot the system (see Figure 1).NetBIOS
Prior to Windows 2000 and DNS, NetBIOS was the method used by Windows for name resolution. Unless your network is running Windows NT systems, it is pretty safe to stop using the NetBIOS functionality. Check out this article for step by step instructions for removing NetBios from Windows 2000/XP/2003 systems.
LLMNR
 Link-local Multicast Name Resolution (LLMNR) is used to connect devices when a well established network is not available. It’s used by both IPv4 and IPv6 networks when services such as DNS and DHCP are not available. Ever notice your Windows system auto configures a169.254.0.XXX address when the network isn’t available? This allows devices connected via a hub, switch or cross cable to get some connectivity. If your users are always on a working LAN, this protocol may be unnecessary.
Link-local Multicast Name Resolution (LLMNR) is used to connect devices when a well established network is not available. It’s used by both IPv4 and IPv6 networks when services such as DNS and DHCP are not available. Ever notice your Windows system auto configures a169.254.0.XXX address when the network isn’t available? This allows devices connected via a hub, switch or cross cable to get some connectivity. If your users are always on a working LAN, this protocol may be unnecessary.Pragmatic General Multicast (PGM) is a reliable and scalable multicast protocol. PGM is appropriate for applications that require duplicate-free multicast data delivery from multiple sources to multiple receivers. Not doing multicast? Then you do not need this protocol.
Find Unnecessary Protocols
To find out if your network is running any of the previously mentioned protocols (or any others you may not need), try using a packet sniffer. I’ve used WireShark (a commonly used packet sniffer), but have also heard that Microsoft Network monitor, which shows the process name of the application that is creating the traffic, is being commonly used. You can get both of these products for free:
Start your packet sniffer and collect a reasonable sample size, such as 20-30 minutes of data. Then simply sort or filter by protocol, and see which ones are on your network and causing unwanted traffic. Then simply remove the unwanted protocols to improve network speed and performance. Try this approach and let us know how well it works for you.
Thursday, October 29, 2009
Simple Network Management with Syslog
How do you easily track thousands of network elements and separate truly critical problems from ordinary network events? No easy task, I know. What approach do you use?
I’m a big fan of using syslog to automatically collect event messages from network devices, rather than monitor devices individually. Over the years, the syslog protocol has become an industry standard for creating, sending and collecting event messages.
A standard syslog message includes the following information:
- Facility type (OS, app or service) that originated the message
- Severity level associated with the message
- Date and time the message was sent
- Hostname or IP address of the sending server or network device
- Message text containing the event description
OS’s, applications and services continuously send these messages to centralized syslog servers. Depending on the capabilities of a particular syslog server, syslog messages can be sorted and viewed according to criteria such as message source, event severity or key words in the message text. Isn’t that convenient?
Also, the syslog server may filter syslog messages and raise alarms based on severity level. These alarms let you deal with unstable network elements first and the respective syslog messages give you the details to understand the source of the problem.
Seems simple right? One challenge is that sifting through a ton of syslogs to troubleshoot a single problem can take hours. You need a way to consolidate, analyze and visualize the information to reduce system downtime and increase network performance. We have a great way for you to see your network status at a glance, check out dVUE6, a cool desktop gadget (for XP and Vista) that monitors the availability and alarm status of your five most alarmed devices in your network. For more information, and to download the gadget, follow this link.
Here is a graphical view of dVUE6
I’m a big fan of using syslog to automatically collect event messages from network devices, rather than monitor devices individually. Over the years, the syslog protocol has become an industry standard for creating, sending and collecting event messages.
A standard syslog message includes the following information:
- Facility type (OS, app or service) that originated the message
- Severity level associated with the message
- Date and time the message was sent
- Hostname or IP address of the sending server or network device
- Message text containing the event description
OS’s, applications and services continuously send these messages to centralized syslog servers. Depending on the capabilities of a particular syslog server, syslog messages can be sorted and viewed according to criteria such as message source, event severity or key words in the message text. Isn’t that convenient?
Also, the syslog server may filter syslog messages and raise alarms based on severity level. These alarms let you deal with unstable network elements first and the respective syslog messages give you the details to understand the source of the problem.
Seems simple right? One challenge is that sifting through a ton of syslogs to troubleshoot a single problem can take hours. You need a way to consolidate, analyze and visualize the information to reduce system downtime and increase network performance. We have a great way for you to see your network status at a glance, check out dVUE6, a cool desktop gadget (for XP and Vista) that monitors the availability and alarm status of your five most alarmed devices in your network. For more information, and to download the gadget, follow this link.
Here is a graphical view of dVUE6
Labels:
Army Network Management,
dVUE,
network gadget,
syslog,
syslog management
Thursday, October 22, 2009
What is Fueling Future Network Growth? Your Thoughts...
 What do you think is driving future network growth?According to a new Cisco study, many residential, business, and mobile IP networking trends are being driven largely by a combination of video, social networking and advanced collaboration applications, termed “visual” networking traffic.
What do you think is driving future network growth?According to a new Cisco study, many residential, business, and mobile IP networking trends are being driven largely by a combination of video, social networking and advanced collaboration applications, termed “visual” networking traffic. Service provider networks are carrying a significant amount of visual networking traffic, with more than one-third of the average global broadband connection supporting video, social networking and collaboration applications each month. Maybe social networking isn’t a fad.
Cisco VNI (Visual Networking Index) Usage Highlights:
Aggregate Broadband Findings (Q3CY09):
- Globally, the average broadband connection (primarily residential subscribers and some business users) generates approximately 11.4 gigabytes of Internet traffic per month.
Per connection per day, this amount is roughly equivalent to downloading 3,000 text emails, 100 MP3 music files or 360 text-only e-books.)
- Globally, the average broadband connection consumes about 4.3 gigabytes of visual networking applications advanced services such as video, social networking and collaboration) traffic per month.
Per connection per day, this amount is roughly the equivalent of approximately 20.5 short-form Internet videos or approximately 1.1 hours of Internet video, whether streamed on its own, embedded in a Web page, or viewed as part of video communications.)
- Top 1 percent of global subscribers generated more than 20 percent of all traffic.
- Top 10 percent of global subscribers generated more than 60 percent of all traffic.
Peak Broadband Usage During Internet Prime Time:
- In an average day over the reported quarter, Internet "prime time" spans from approximately 9 p.m to 1 a.m. around the world. This contrasts with broadcast TV prime time, which is generally from 7 p.m. to 11 p.m. across most global markets.
- 25 percent (or 93.3 megabytes per day per connection) of global Internet traffic is generated during the Internet "prime time" period.
- A peak Internet hour has 20 percent more traffic than a nonpeak Internet hour. The peak Internet hour averages 18 megabytes of traffic per connection (per hour), while nonpeak Internet hours average 15 megabytes of traffic per connection (per hour).
The peak Internet visual networking hour has almost 25 percent more traffic than average hourly Internet traffic.
It’s one thing to imagine the amount of traffic passing through networks every day, but it’s another to actually see the numbers. My favorite statistic is the number of GBs used per connection per day compared to text messages, e-books and music. The numbers are huge! I can’t imagine sending 3,000 text messages per day, can you?
What do you think about these findings? What are the future implications? I’m interested in hearing your thoughts.
Friday, October 16, 2009
Network Disaster Preparedness Tips
With the winter season approaching, big storms bringing everything from heavy rain and lightning to snow and wind will be a constant threat to network operations. When was the last time your local IT team reviewed disaster preparedness procedures? Now is a great time to start. If any form of a disaster hits, do you or your team know your capabilities and how to react? Here are some important questions that your IT team should be able to answer and use to improve your disaster procedures:
1. Are you aware of your power situation?
a. What happens when a power outage occurs?
b. What is the operational status of the UPS system?
c. How long will the UPS backup systems sustain key functions?
d. What do we do if the outage is longer?
2. What if the building becomes unavailable? (fire or water damage)
a. Are the offsite backups current?
b. If a network device or server is ruined, what is the procedure to replace it?
c. Does everyone know the primary and secondary facility contacts to use should an after-hours emergency occur?
3. What if access to the building is limited? (snow, tornado warnings, etc)
a. Is VPN access updated for all employees that may need to work from home?
b. Can all of the required maintenance procedures be done remotely or skipped for several days?
4. What if the phone and/or Internet connection is lost?
5. What is the customer impact when any of these conditions occur?
Advance planning is the best approach. A good network design can minimize the impact of storm and disaster related problems. Having redundant phone and data lines from different carriers minimizes the inbound/outbound traffic risk. Using an adequate number of UPS devices mitigates all but very lengthy power outages and network routing protocols like HSRP reduce the risk of single device point of failures.
Even monitoring your network with disaster prevention in mind can be helpful in avoiding unnecessary failures. These tips are a great starting point:
a. What happens when a power outage occurs?
b. What is the operational status of the UPS system?
c. How long will the UPS backup systems sustain key functions?
d. What do we do if the outage is longer?
2. What if the building becomes unavailable? (fire or water damage)
a. Are the offsite backups current?
b. If a network device or server is ruined, what is the procedure to replace it?
c. Does everyone know the primary and secondary facility contacts to use should an after-hours emergency occur?
3. What if access to the building is limited? (snow, tornado warnings, etc)
a. Is VPN access updated for all employees that may need to work from home?
b. Can all of the required maintenance procedures be done remotely or skipped for several days?
- Enable redundant polling of critical devices
- Map out HSRP primary and secondary links
- Know the status of the UPS systems
- Make sure you have 24x7 access to your management system client
If you have tips for network disaster prepardeness, please share them with us.
Wednesday, October 14, 2009
Resolve Network Problems Faster with Wireshark
I’m a big fan of Wireshark, an open source tool to capture and analyze network traffic. Wireshark can be very helpful in terms of network troubleshooting and analysis. I recently came across a great tip from Chris Greer, a Senior Network Analyst on how to add useful columns, as well as recommendations for which columns are most commonly used (detailed below). If you have any tips that you would like to share to help network managers, please send them along.
What are the best columns to display?
Wireshark allows you to easily display specific packet data in the summary view. Depending on the problem you are looking for, it may be useful to add or remove custom columns so you only see information that will really help you solve the problem. For example, it’s not always useful to display the IP identification number for every packet in the trace file as a column on the top of the screen. But, one thing that is quite useful to display for most problems is the size of each packet.
How to add and remove columns.
Open up any trace file in Wireshark. At first, in the top screen, you will see a frame number, a time column (usually elapsed time from the start of the capture), source and destination addresses, what protocol is used, and finally a summary of what the packet contains. While this data is great to start out with, it won’t take long before adding a column of specific data will help.
To add a column, select Edit Preferences. This will bring up the Preferences window where Columns can be selected from the left. The default columns will be displayed here. To add a column, click the Add button and select the desired information to add from the format menu. Name the column and then you are done.
For example, to add the packet length, select add, name the column Length, then select Packet Length from the Format Bar. By default, it will be added at the bottom of the list, which will make it appear on the far right of the summary view. To move it up, just drag and drop it up where it can be more easily seen, such as between the destination and protocol fields.
After adding the column, click the apply button and the length of the packet will now be displayed in the summary view of Wireshark.
What are the most useful columns?
This of course depends on what problem you are trying to resolve. Here are the ones I use with a description of why:
Delta Time - Handy to have in just about any situation. It is needed for measuring server response time, network roundtrip time, and other delays. Delta time can be displayed by modifying the already present time column in the View menu, or by adding delta time as its own column.
Cumulative Bytes – When moving large blocks of data, this column displays how much data has been sent. You can then divide by the time it took to send it and figure out the throughput used by the application.
In this data copy, after filtering on one direction of traffic and resetting the timers, we find that in .022 seconds, there was 193,220 bytes sent. (193,200 x 8)/.022 = Bitrate. This transfer took up 70Mbps of my line. Very useful when looking at backups!
TCP Window Size – Useful when TCP Window size is an issue, usually in larger file transfers. It can be added by selecting Custom from the column menu, then entering tcp.window_size in the field name. This column will show when and how often the TCP window drops, without needing to dig for this value in the packet details.
Using these columns makes it easier to spot problems in the summary view. They save you from needing to dig deep into every packet for a specific field, which saves a ton of time when troubleshooting!
What are the best columns to display?
Wireshark allows you to easily display specific packet data in the summary view. Depending on the problem you are looking for, it may be useful to add or remove custom columns so you only see information that will really help you solve the problem. For example, it’s not always useful to display the IP identification number for every packet in the trace file as a column on the top of the screen. But, one thing that is quite useful to display for most problems is the size of each packet.
How to add and remove columns.
Open up any trace file in Wireshark. At first, in the top screen, you will see a frame number, a time column (usually elapsed time from the start of the capture), source and destination addresses, what protocol is used, and finally a summary of what the packet contains. While this data is great to start out with, it won’t take long before adding a column of specific data will help.
To add a column, select Edit Preferences. This will bring up the Preferences window where Columns can be selected from the left. The default columns will be displayed here. To add a column, click the Add button and select the desired information to add from the format menu. Name the column and then you are done.
After adding the column, click the apply button and the length of the packet will now be displayed in the summary view of Wireshark.
What are the most useful columns?
This of course depends on what problem you are trying to resolve. Here are the ones I use with a description of why:
Delta Time - Handy to have in just about any situation. It is needed for measuring server response time, network roundtrip time, and other delays. Delta time can be displayed by modifying the already present time column in the View menu, or by adding delta time as its own column.
Cumulative Bytes – When moving large blocks of data, this column displays how much data has been sent. You can then divide by the time it took to send it and figure out the throughput used by the application.
In this data copy, after filtering on one direction of traffic and resetting the timers, we find that in .022 seconds, there was 193,220 bytes sent. (193,200 x 8)/.022 = Bitrate. This transfer took up 70Mbps of my line. Very useful when looking at backups!
TCP Window Size – Useful when TCP Window size is an issue, usually in larger file transfers. It can be added by selecting Custom from the column menu, then entering tcp.window_size in the field name. This column will show when and how often the TCP window drops, without needing to dig for this value in the packet details.
IP TOS (DiffSrv) – When monitoring traffic using the TOS field, such as VoIP, this column is helpful in viewing what bits are set and if QoS is configured for this value. It can be added selecting the IP DSCP Value option.
Using these columns makes it easier to spot problems in the summary view. They save you from needing to dig deep into every packet for a specific field, which saves a ton of time when troubleshooting!
Friday, October 9, 2009
Announcing the release of dopplerVUE 2.0
dopplerVUE 2.0 is now available for download with exciting new features including discovering and mapping HSRP primary and secondary links, a new interface with graphics for better visibility, improved SNMP table polling and more! The 30-day trial is free, just like it was for the pre-release.
OPSCenter Screenshot

Netflow Screenshot

For those of you who missed the pre-release announcement, here’s the new feature list:
OPSCenter Screenshot

Netflow Screenshot

For those of you who missed the pre-release announcement, here’s the new feature list:
- New interface with new graphics for better readability
- Manage ANY metric on ANY device with improved SNMP table polling
- Discover and map HSRP primary and secondary links
- New WMI wizard
- Easily create personal workspaces with the new dVUE templates
- Distributed architecture to extend the number of managed devices
- Improved database and architecture for increased performance
Plus - for distributed enterprise networks dopplerVUE connects with NeuralStar to create a two-tiered, centrally monitored, fully replicated enterprise network management system that provides:
- Increased fault tolerance
- Improved performance through load balancing
- Powerful disaster recovery capabilities
- Enhanced scalability
I’d love to hear any dopplerVUE or network-related comments or questions you have!
Wednesday, October 7, 2009
IT Hiring Improving?
Here are some interesting data points about IT hiring from an industry article I just read. As usual there are some mixed indicators, but hopefully the market continues to improve.
• IT unemployment rate (5.5%) is only about half the overall market (9.8%)
• IT budgets are expected to grow a bit in 2010 (IDC predicts 2.9% growth and Gartner estimates a 1.53% increase)
• Hiring is increasing in areas including New York, Washington, D.C., Chicago, Los Angeles, Dallas and Houston (according to Robert Half Technology)
• Robert Half reports that health care organizations plan to increase IT hiring by 5 percent in the fourth quarter, while overall IT hiring is expected to remain flat
• Network security, especially securing government data, is one of the most desired skills (according to Dice.com)
• Many projects with higher paying skills have been put off, but the associated skills remain in demand : .Net, ERP development, SharePoint development, Virtualization (according to Dice.com and Robert Half Technology)
• Much of the hiring is occurring on the desktop side, desktop support analysts, PC techs, as well as program analysts and web development (according to Robert Half Technology)
If you’re looking for open positions, check out the careers section of our website. We currently have a web developer position open as well as many other IT positions in various geographic locations.
• IT unemployment rate (5.5%) is only about half the overall market (9.8%)
• IT budgets are expected to grow a bit in 2010 (IDC predicts 2.9% growth and Gartner estimates a 1.53% increase)
• Hiring is increasing in areas including New York, Washington, D.C., Chicago, Los Angeles, Dallas and Houston (according to Robert Half Technology)
• Robert Half reports that health care organizations plan to increase IT hiring by 5 percent in the fourth quarter, while overall IT hiring is expected to remain flat
• Network security, especially securing government data, is one of the most desired skills (according to Dice.com)
• Many projects with higher paying skills have been put off, but the associated skills remain in demand : .Net, ERP development, SharePoint development, Virtualization (according to Dice.com and Robert Half Technology)
• Much of the hiring is occurring on the desktop side, desktop support analysts, PC techs, as well as program analysts and web development (according to Robert Half Technology)
If you’re looking for open positions, check out the careers section of our website. We currently have a web developer position open as well as many other IT positions in various geographic locations.
Labels:
Information Technology,
IT,
IT hiring,
IT positions,
Open positions
Thursday, October 1, 2009
Before Adding More Bandwidth…
Does your network reach capacity at similar times every day? If so, before you decide to add more bandwidth at additional cost, think about adjusting traffic patterns at no cost.
As a first step, consider using a network monitoring tool to baseline the most common time periods when your network is at capacity. With this critical information, you can take some pro-active steps to optimize your network traffic.
Move maintenance tasks such as back-ups, updates, source control synchronization and large file transfers to off peak periods to decrease the load on the network.
If you can’t alter the timeline for maintenance tasks, encourage users to schedule bandwidth intensive tasks (video teleconferencing and webcasts) that are not time sensitive to business operations to off peak periods. Most users want the best possible viewing experience and will appreciate being able to schedule online events to take advantage of improved network availability.
Of course, if you don’t have flexibility to adjust traffic patterns to optimize the network, it may be time to add more bandwidth.
As a first step, consider using a network monitoring tool to baseline the most common time periods when your network is at capacity. With this critical information, you can take some pro-active steps to optimize your network traffic.
Move maintenance tasks such as back-ups, updates, source control synchronization and large file transfers to off peak periods to decrease the load on the network.
If you can’t alter the timeline for maintenance tasks, encourage users to schedule bandwidth intensive tasks (video teleconferencing and webcasts) that are not time sensitive to business operations to off peak periods. Most users want the best possible viewing experience and will appreciate being able to schedule online events to take advantage of improved network availability.
Of course, if you don’t have flexibility to adjust traffic patterns to optimize the network, it may be time to add more bandwidth.
Tuesday, September 29, 2009
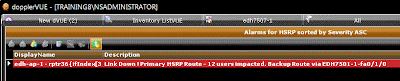
3 Key Steps to Actively Monitoring HSRP…
I recently discussed how to build a resilient network using HSRP/VRRP and as a follow-up, here are a few key steps to actively monitoring HSRP.
With HSRP on our network, there is a good deal of network reliability for end users. As the network engineer, this means when a link fails, end users rarely notice it. The backup link simply handles the load and business continues as usual. Just the way I want it. While my monitoring system does provide an alert to the link down condition, I like to handle these situations as a higher priority, since it has become a single point of failure.
Here are a few tips to actively managing your HSRP implementation:
1. Map out each pair – know when a primary route goes out, what path has been designated as the alternate (if you have many HSRP routes you can combine them onto a single map. The pre-created map makes it easy to find the paired item).
2. Create custom alerts for HSRP interfaces that indicate which path is a primary or secondary HSRP link. The HSRP interfaces need to be treated differently than a switch port to a user workstation due to their critical nature.
3. After service has been restored, review the interface load of the secondary link and evaluate how well it handled the traffic. Use this information to ensure your backup pipes have adequate capacity. This will improve your disaster recovery planning for any future events.
Here are some monitoring screenshots that show my HSRP map and an active alarm.
With HSRP on our network, there is a good deal of network reliability for end users. As the network engineer, this means when a link fails, end users rarely notice it. The backup link simply handles the load and business continues as usual. Just the way I want it. While my monitoring system does provide an alert to the link down condition, I like to handle these situations as a higher priority, since it has become a single point of failure.
Here are a few tips to actively managing your HSRP implementation:
1. Map out each pair – know when a primary route goes out, what path has been designated as the alternate (if you have many HSRP routes you can combine them onto a single map. The pre-created map makes it easy to find the paired item).
2. Create custom alerts for HSRP interfaces that indicate which path is a primary or secondary HSRP link. The HSRP interfaces need to be treated differently than a switch port to a user workstation due to their critical nature.
3. After service has been restored, review the interface load of the secondary link and evaluate how well it handled the traffic. Use this information to ensure your backup pipes have adequate capacity. This will improve your disaster recovery planning for any future events.
Here are some monitoring screenshots that show my HSRP map and an active alarm.
Wednesday, September 23, 2009
Looking to Reduce IT Costs…Optimize Network Traffic
In these days of pinching pennies and saving dimes, the best way to help your organization is to find ways to reduce costs. Do you know which network resources are costing you the most? Answering this question can lead to optimizing network traffic and cutting costs.
For instance, the cost of LAN traffic within your office is usually fairly affordable, however, once the packets hit the WAN, the price tag increases significantly.
You can use Netflow to identify which network resources are adding the most to your monthly bill. Start monitoring the circuits that make up the majority of your high cost list with Netflow and you might find some network efficiencies that lead to savings that have a big financial impact.
To find cost savings, I use a network management tool, dopplerVUE, that has a bandwidth locator that sorts and finds top bandwidth users in networks. dopplerVUE provides Netflow support to give you multiple ways to view traffic in your network.
If you want more details on where all your traffic is going and how to configure Netflow to give you the answers, check out this recent post.
For instance, the cost of LAN traffic within your office is usually fairly affordable, however, once the packets hit the WAN, the price tag increases significantly.
You can use Netflow to identify which network resources are adding the most to your monthly bill. Start monitoring the circuits that make up the majority of your high cost list with Netflow and you might find some network efficiencies that lead to savings that have a big financial impact.
To find cost savings, I use a network management tool, dopplerVUE, that has a bandwidth locator that sorts and finds top bandwidth users in networks. dopplerVUE provides Netflow support to give you multiple ways to view traffic in your network.
If you want more details on where all your traffic is going and how to configure Netflow to give you the answers, check out this recent post.
Friday, September 18, 2009
Pre-Release of dopplerVUE 2.0 Now Available
To piggyback on the post last week about HSRP, I’d like to share that the pre-release of dopplerVUE 2.0 is available for download. dopplerVUE 2.0 has exciting new features including discovering and mapping HSRP primary and secondary links, a new interface with graphics for better visibility, improved SNMP table polling and more! The 30-day trial is free, and who doesn’t like free?
Here is the new feature list:
- New interface with new graphics for better readability
- Manage ANY metric on ANY device with improved SNMP table polling
- Discover and map HSRP primary and secondary links
- New WMI wizard
- Easily create personal workspaces with the new dVUE templates
- Distributed architecture to extend the number of managed devices
- Improved database and architecture for increased performance
Plus - for distributed enterprise networks dopplerVUE connects with NeuralStar to create a two-tiered, centrally monitored, fully replicated enterprise network management system that provides:
Increased fault tolerance
- Improved performance through load balancing
- Powerful disaster recovery capabilities
- Enhanced scalability
If you decide to check it out and have questions, please don’t hesitate to post here in the blog or send me a message! I’m happy to help with network related questions.
Here are a couple of screen shots of the new dopplerVUE interface:
Thursday, September 17, 2009
Three Easy Techniques for Cutting Alarm Clutter
Have you ever missed (or almost missed) a critical network alarm that could have prevented a serious network performance or availability problem because it was hidden among non-essential alarms? Hopefully the answer is no, but the situation highlights a serious problem – “alarm clutter”.
Today’s network devices and servers are capable of providing a dizzying set of alarms on almost anything from packet errors to available memory. That’s a lot of power for troubleshooting and problem solving, but it can also mean that even in a small network of only a few hundred elements you can become overwhelmed by a storm of alarms.
Here are three easy techniques for managing the volume of alarms and their relative severity. Using them in the right circumstances can help you find and fix problems more quickly by spending less time wading through a sea of distractions.
Technique 1: Duration-based alarming
Duration-based alarming is a common technique for reducing the number of alarms from a particular device or server. Instead of reporting every instance of an alarm condition, an alarm is issued only if the condition persists for an unusual period of time.
For example, suppose interface utilization on a router occasionally exceeds 90% every few minutes. Normally, this wouldn’t be a concern and an alarm isn’t warranted (in fact, it could mean the router is optimally “sized” for the expected or nominal level of traffic for the interface). On the other hand, if interface utilization exceeds 90% for 15 minutes or more, a bottleneck has developed and an alarm should be generated. With duration based alarming, you are notified only when an actual problem develops—not every time a short, transient condition occurs.
Technique 2: Average-value alarming
Average-value alarming offers a similar approach. Instead of creating an alarm every time a measure exceeds a pre-determined threshold, an alarm is issued only if the average value of the measure over time exceeds the threshold.
It’s not uncommon, for example, to see processor utilization periodically “spike” at 100% for a few seconds. However, if a processor experiences an average of 90% utilization for 20 minutes that would be cause for concern and you would fully expect an alarm.
Technique 3: Severity-level alarming
Rather than setting just one alarm threshold, try setting multiple threshold values that represent increasing levels of severity.
Disk space used, for example, increases gradually to the point where applications can no longer function. Obviously, you want an alarm when available disk space is at 90%, but wouldn’t it be helpful to know when disk space is at 70% and then 80% so you have time to “clean up” the disk before applications suffer? You could configure a minor alarm when available disk space is at 70%, a major alarm at 80%, and finally a critical alarm at 90%.
These are just three of the most useful ways to reduce alarm clutter to focus on actionable alarms. Using them will help you identify significant network issues earlier, before users are impacted.
Today’s network devices and servers are capable of providing a dizzying set of alarms on almost anything from packet errors to available memory. That’s a lot of power for troubleshooting and problem solving, but it can also mean that even in a small network of only a few hundred elements you can become overwhelmed by a storm of alarms.
Here are three easy techniques for managing the volume of alarms and their relative severity. Using them in the right circumstances can help you find and fix problems more quickly by spending less time wading through a sea of distractions.
Technique 1: Duration-based alarming
Duration-based alarming is a common technique for reducing the number of alarms from a particular device or server. Instead of reporting every instance of an alarm condition, an alarm is issued only if the condition persists for an unusual period of time.
For example, suppose interface utilization on a router occasionally exceeds 90% every few minutes. Normally, this wouldn’t be a concern and an alarm isn’t warranted (in fact, it could mean the router is optimally “sized” for the expected or nominal level of traffic for the interface). On the other hand, if interface utilization exceeds 90% for 15 minutes or more, a bottleneck has developed and an alarm should be generated. With duration based alarming, you are notified only when an actual problem develops—not every time a short, transient condition occurs.
Technique 2: Average-value alarming
Average-value alarming offers a similar approach. Instead of creating an alarm every time a measure exceeds a pre-determined threshold, an alarm is issued only if the average value of the measure over time exceeds the threshold.
It’s not uncommon, for example, to see processor utilization periodically “spike” at 100% for a few seconds. However, if a processor experiences an average of 90% utilization for 20 minutes that would be cause for concern and you would fully expect an alarm.
Technique 3: Severity-level alarming
Rather than setting just one alarm threshold, try setting multiple threshold values that represent increasing levels of severity.
Disk space used, for example, increases gradually to the point where applications can no longer function. Obviously, you want an alarm when available disk space is at 90%, but wouldn’t it be helpful to know when disk space is at 70% and then 80% so you have time to “clean up” the disk before applications suffer? You could configure a minor alarm when available disk space is at 70%, a major alarm at 80%, and finally a critical alarm at 90%.
These are just three of the most useful ways to reduce alarm clutter to focus on actionable alarms. Using them will help you identify significant network issues earlier, before users are impacted.
Friday, September 11, 2009
Building a resilient network using HSRP/VRRP
A group of key servers losing network connectivity can lead to a real bad day. You can improve your network routing resiliency by adding hot-standby routers and HSRP (Hot Standby Routing Protocol) or use a similar method such as VRRP (Virtual Router Redundancy Protocol) for non-Cisco devices. HSRP provides a straightforward approach by having two physical routers accessible by any given switch. It’s a great approach to improving the reliability of your key equipment. Here are some quick basics on how it works:
1. Two routers share a virtual IP address that is used as the gateway IP.
2. A primary and secondary router are designated with each given a priority number. The primary router priority number is higher than the secondary router.
3. The primary router sends a Hello packet to the secondary on a timed basis. If this packet is not received then the secondary becomes the primary. Very low packet loss occurs during a failover and most transmissions using TCP are completed seamlessly due to the re-try mechanism. The re-try mechanism can be controlled by adjusting the length of the time between Hello packets.
4. Once back online, the primary router sends out a notification that includes its priority number. The router with the highest priority number becomes the primary.

1. Two routers share a virtual IP address that is used as the gateway IP.
2. A primary and secondary router are designated with each given a priority number. The primary router priority number is higher than the secondary router.
3. The primary router sends a Hello packet to the secondary on a timed basis. If this packet is not received then the secondary becomes the primary. Very low packet loss occurs during a failover and most transmissions using TCP are completed seamlessly due to the re-try mechanism. The re-try mechanism can be controlled by adjusting the length of the time between Hello packets.
4. Once back online, the primary router sends out a notification that includes its priority number. The router with the highest priority number becomes the primary.

This process can be used in groups with multiple routers offering to become the primary router in the event of a failure. Some devices even support using the same interface for multiple groups. This can be helpful when cross connecting multiple departments and to minimize the amount of duplicate hardware necessary.
The following is a sample set of IOS commands necessary to implement HSRP.
Router> enable
Router# configure terminal
Router(config)# interface ethernet 0
Router(config-if)# ip address 172.16.6.5
255.255.255.0
Router(config-if)# standby 1 ip 172.16.6.100
Router(config-if)# end
Router# show standby
Router# show standby ethernet 0
For more information review the Cisco documentation.
The following is a sample set of IOS commands necessary to implement HSRP.
Router> enable
Router# configure terminal
Router(config)# interface ethernet 0
Router(config-if)# ip address 172.16.6.5
255.255.255.0
Router(config-if)# standby 1 ip 172.16.6.100
Router(config-if)# end
Router# show standby
Router# show standby ethernet 0
For more information review the Cisco documentation.
Thursday, September 10, 2009
Looking Forward to the Modern Day Marine Show
I’ve attended a lot of events lately, and it’s not over yet! I’ll be attending the Modern Day Marine show, held September 29th – October 1st in Quantico, Virginia. The show focuses on systems and technology, but also caters to equipment and services, making it attractive for all areas of interest. It looks like there are a good number of vendors exhibiting (there are three large tents and an outside exhibitor area), and a few events outside of the expo such as a large Robotics Rodeo and a grand banquet and reception.
This should be a great opportunity to hear more about the U.S. Marine Corps wants and needs in the network management space. It will also be a great venue to get feedback on the upcoming dopplerVUE 2.0 and NeuralStar 9.5 releases. Keep your eyes peeled for my post-show report in early October. Stay tuned for more information on the new release later this week!
Think you might be interested in attending Modern Day Marine? Check it out, here. There will also be two additional Marine Military Expos, Marine South and Marine West, held in 2010.
This should be a great opportunity to hear more about the U.S. Marine Corps wants and needs in the network management space. It will also be a great venue to get feedback on the upcoming dopplerVUE 2.0 and NeuralStar 9.5 releases. Keep your eyes peeled for my post-show report in early October. Stay tuned for more information on the new release later this week!
Think you might be interested in attending Modern Day Marine? Check it out, here. There will also be two additional Marine Military Expos, Marine South and Marine West, held in 2010.
Thursday, September 3, 2009
A Tip for Managing Wired Networks
Earlier in the week, I posted three tips for managing wireless networks. Thought I would also share a tip for managing wired networks to round things out for the week. Here is a response to a question I often get from customers.
How can I tell when a Cisco device configuration has been altered or accessed?
You can be notified of any configuration changes or attempts by enabling the CiscoConfigManEvent trap. This feature sends you a trap whenever a user exits the configuration session. Simply point the trap to your network management system to see when somebody accesses a Cisco configuration session.
For dopplerVUE Users
You can forward traps as an email for 24x7 instant access to changes on network devices. To read more about this trap and how to configure it, please reference the following Cisco article.
How can I tell when a Cisco device configuration has been altered or accessed?
You can be notified of any configuration changes or attempts by enabling the CiscoConfigManEvent trap. This feature sends you a trap whenever a user exits the configuration session. Simply point the trap to your network management system to see when somebody accesses a Cisco configuration session.
For dopplerVUE Users
You can forward traps as an email for 24x7 instant access to changes on network devices. To read more about this trap and how to configure it, please reference the following Cisco article.
Tuesday, September 1, 2009
3 Tips for Managing Wireless Networks
The convenience of wireless networks can’t be underestimated. In today’s environment, mobile computing is an expectation. So when users run into connectivity and bandwidth issues, you can be sure that complaints are soon to follow. Here are three tips for managing wireless networks to help you avoid some potential headaches.
1. Improve wireless connectivity to the access point
If users frequently lose their wireless signal it’s going to be a frustrating situation. When wireless coverage drops, check for an increase in environmental disruptions. Look for Bluetooth headsets, video cameras and microwaves. These personal wireless devices can cause interference and often are the culprits.
If users still cannot connect reliably (or they were never able to connect at all), you may have a coverage problem, which frequently can be fairly easy to resolve. Use a laptop and the wireless strength meter to map coverage holes in your wireless system. Some free tools such as Netstumbler provide detailed graphs of signal strength and noise level. In addition, periodically perform a laptop survey to find rogue wireless routers to limit their use and ensure optimal network performance. Simply use the same laptop and wireless utility to scan for wireless networks for various points within your buildings.
2. Tracking the availability of the wireless access point
This is the intersection between wired and wireless network management. At a minimum, periodically ping all wireless access points to check their up and down status, making sure they are working and can interconnect to the wired network. Some network management tools like dopplerVUE let you do this on a regular schedule. For SNMP enabled wireless devices such as the Cisco 1200 series, you will also be able to monitor the CPU load and other metrics to know when the device is overloaded, slowing down or dropping all traffic on the access point.
3. Assure sufficient bandwidth to the access point
Once you know users have a decent connection, managing bandwidth may become an issue. Many wireless systems can handle 20 or more users. Monitoring each user on an ad hoc network is likely to be of limited value. Since all users are funneling through the same fixed wire connection, monitoring bandwidth where your access point connects to the network will provide a good summary of the traffic volume. This will help you understand when to upgrade a system and alert you before users call to complain about connectivity issues.
Tip for dopplerVUE users:
For a better understanding of when your network is busy, include wireless access points in your managed network inventory. dopplerVUE will monitor them for their up and down status and core system performance such as CPU load. Use the bandwidth usage finder to watch the real time traffic flow, comparing performance to the automatic benchmarks calculated by dopplerVUE. You will always know the availability status of your wireless access points and how much traffic is generated on each.
1. Improve wireless connectivity to the access point
If users frequently lose their wireless signal it’s going to be a frustrating situation. When wireless coverage drops, check for an increase in environmental disruptions. Look for Bluetooth headsets, video cameras and microwaves. These personal wireless devices can cause interference and often are the culprits.
If users still cannot connect reliably (or they were never able to connect at all), you may have a coverage problem, which frequently can be fairly easy to resolve. Use a laptop and the wireless strength meter to map coverage holes in your wireless system. Some free tools such as Netstumbler provide detailed graphs of signal strength and noise level. In addition, periodically perform a laptop survey to find rogue wireless routers to limit their use and ensure optimal network performance. Simply use the same laptop and wireless utility to scan for wireless networks for various points within your buildings.
2. Tracking the availability of the wireless access point
This is the intersection between wired and wireless network management. At a minimum, periodically ping all wireless access points to check their up and down status, making sure they are working and can interconnect to the wired network. Some network management tools like dopplerVUE let you do this on a regular schedule. For SNMP enabled wireless devices such as the Cisco 1200 series, you will also be able to monitor the CPU load and other metrics to know when the device is overloaded, slowing down or dropping all traffic on the access point.
3. Assure sufficient bandwidth to the access point
Once you know users have a decent connection, managing bandwidth may become an issue. Many wireless systems can handle 20 or more users. Monitoring each user on an ad hoc network is likely to be of limited value. Since all users are funneling through the same fixed wire connection, monitoring bandwidth where your access point connects to the network will provide a good summary of the traffic volume. This will help you understand when to upgrade a system and alert you before users call to complain about connectivity issues.
Tip for dopplerVUE users:
For a better understanding of when your network is busy, include wireless access points in your managed network inventory. dopplerVUE will monitor them for their up and down status and core system performance such as CPU load. Use the bandwidth usage finder to watch the real time traffic flow, comparing performance to the automatic benchmarks calculated by dopplerVUE. You will always know the availability status of your wireless access points and how much traffic is generated on each.
Subscribe to:
Posts (Atom)